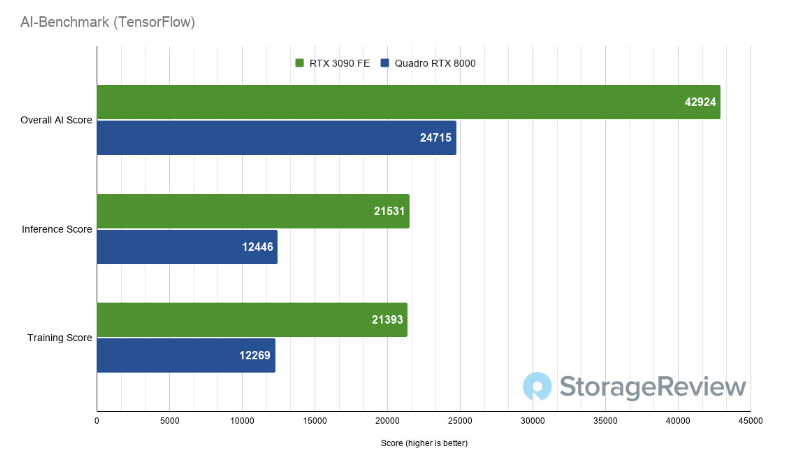
Online gpu for machine learning is revolutionizing the way data scientists and developers approach complex computational tasks. In a world where artificial intelligence is steadily becoming integral to various industries, the demand for efficient processing power that GPUs provide is at an all-time high. These powerful units enable faster training of models, improved performance, and the ability to handle large datasets seamlessly.
By leveraging the capabilities of online GPUs, users can access cutting-edge technology without the need for heavy investment in hardware. This flexibility allows for cost-effective experimentation and scaling of machine learning projects, driving innovation and collaboration among teams worldwide.
In the ever-evolving landscape of technology, the significance of cybersecurity has grown exponentially. With more businesses and individuals relying on digital platforms for their daily operations, the need to protect sensitive information from unauthorized access has never been more critical. Cybersecurity encompasses a range of practices designed to safeguard computers, networks, programs, and data from attack, damage, or unauthorized access.
Let’s delve deeper into this essential field and explore its components, importance, and emerging trends.### The Components of CybersecurityAt its core, cybersecurity is a multi-faceted discipline that includes various components:
1. Network Security
This involves securing a computer network infrastructure. Network security measures include both hardware and software technologies aimed at protecting the integrity, confidentiality, and accessibility of computer networks and data.
2. Application Security
This aspect focuses on keeping software and devices free of threats. A compromised application can provide access to the data it is designed to protect. Security measures can be implemented at the application level, such as writing secure code and conducting regular software updates.
3. Information Security
This protects the integrity and privacy of data, both in storage and in transit. Information security is critical for maintaining the confidentiality of sensitive information such as personal details, financial records, and intellectual property.
4. Endpoint Security
With the increasing number of mobile devices accessing corporate networks, endpoint security has become crucial. This involves securing endpoints, such as mobile devices and laptops, which connect to the corporate network.
5. Identity Management and Data Security
This component involves ensuring that the right individuals have access to the right resources for the right reasons. Strong identity management solutions help organizations control user access and protect sensitive data.
6. Cloud Security
As more organizations migrate their data and services to the cloud, cloud security has become increasingly important. This includes measures to protect cloud-based systems, applications, and data.### The Growing Importance of CybersecurityWith the increasing frequency and sophistication of cyberattacks, the importance of cybersecurity has reached new heights. Major data breaches can lead to significant financial losses, damage to brand reputation, and legal consequences.
Companies like Target and Equifax have faced severe repercussions following high-profile breaches, highlighting the potential fallout from inadequate cybersecurity measures.Furthermore, as more devices become interconnected through the Internet of Things (IoT), the potential attack surface for cybercriminals expands. Every device connected to the internet represents a potential vulnerability, making a comprehensive cybersecurity strategy essential for businesses of all sizes.### Emerging Trends in CybersecurityIn response to the evolving threat landscape, several trends are shaping the future of cybersecurity:
1. Artificial Intelligence and Machine Learning
Cybersecurity solutions are increasingly leveraging AI and machine learning to analyze data patterns and detect anomalies. These technologies can help identify potential threats in real time, allowing organizations to respond more quickly to incidents.
2. Zero Trust Architecture
This security model assumes that threats could be both external and internal. Consequently, it requires strict identity verification for every user and device attempting to access resources on a network. The Zero Trust model emphasizes the idea of “never trust, always verify.”
3. Cybersecurity Awareness Training
Human error remains one of the leading causes of data breaches. Organizations are investing in training programs to educate employees on cybersecurity best practices, helping them recognize phishing attempts and safeguard sensitive information.
4. Regulatory Compliance
With increasing regulations surrounding data protection, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, organizations must prioritize compliance to avoid hefty fines and legal issues.
5. Remote Work Security
The shift to remote work, accelerated by the COVID-19 pandemic, has introduced new cybersecurity challenges. Organizations need to ensure that remote workers can securely access company data without compromising security.### Best Practices for Strengthening CybersecurityTo bolster cybersecurity efforts, organizations can adopt several best practices:
1. Regular Software Updates
Keeping software and systems up to date is crucial in protecting against known vulnerabilities. Regular updates can help patch security holes that attackers might exploit.
2. Strong Password Policies
Implementing policies that encourage or enforce the use of strong, unique passwords can significantly enhance security. Consider using multi-factor authentication (MFA) for an added layer of protection.
3. Data Encryption
Encrypting sensitive data both in transit and at rest can protect it from unauthorized access. Even if data is intercepted, encryption makes it unreadable without the proper decryption key.
4. Incident Response Plan
Developing and maintaining a robust incident response plan ensures that organizations can effectively respond to and recover from cyber incidents. This plan should include procedures for communication, containment, eradication, and recovery.
5. Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and assess the effectiveness of current security measures. These audits should include penetration testing and vulnerability assessments.### ConclusionAs we navigate the complexities of the digital world, cybersecurity remains a critical concern for individuals and organizations alike. With cyber threats continuing to evolve, staying informed about the latest trends and adopting robust security measures is essential.
By prioritizing cybersecurity, organizations can protect their assets, maintain their reputation, and ensure the trust of their customers. In a world where digital transformation is ongoing, cybersecurity will remain a top priority for years to come.
FAQ Resource
What is an online GPU?
An online GPU refers to a cloud-based graphics processing unit that users can access remotely for computational tasks, particularly for machine learning and AI applications.
How does an online GPU improve machine learning performance?
Online GPUs can significantly speed up the training of machine learning models by providing parallel processing capabilities, allowing for faster computations on large datasets.
Are there any costs associated with using online GPUs?
Yes, using online GPUs typically involves pay-as-you-go pricing or subscription fees, depending on the service provider and the level of resources consumed.
Can online GPUs be used for purposes other than machine learning?
Absolutely! Online GPUs are also used for tasks like video rendering, gaming, and scientific simulations, making them versatile tools in high-performance computing.

What should I consider when choosing an online GPU service?
Factors to consider include pricing, performance specifications, ease of integration, support for various frameworks, and available features such as scalability and storage options.